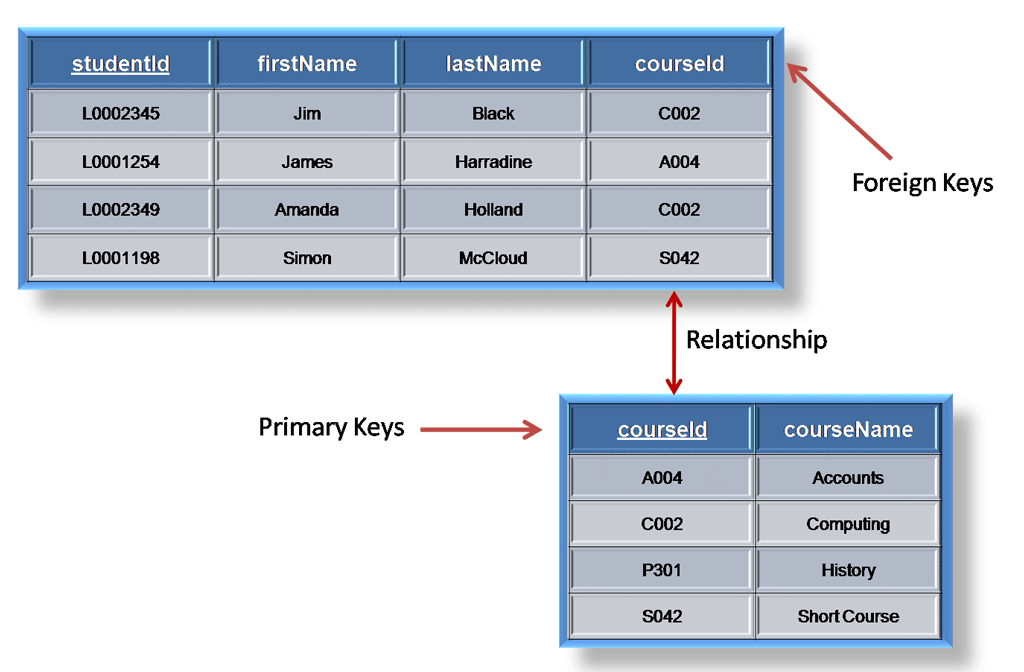
A “key” is one of the most basic and important concepts of the Database Management System (DBMS); the keys helps us work easily with the records and the tables in our database by providing us with the ease of accessing and retrieving the data from the table. A primary key is the first key to be understood as it uniquely identifies the particular record of any table. The primary key and foreign key however, must not be confused with each other as they have a completely different definition as well as usage. Here are the differences between the two.
Difference between Primary Key and Foreign Key
| S.no. | Primary key | Foreign key | |||||||||||||||||||||||||||||||||||
| 1 | The primary key of a particular table is the attribute which uniquely identifies every record and does not contain any null value. | The foreign key of a particular table is simply the primary key of some other table which is used as a reference key in the second table. | |||||||||||||||||||||||||||||||||||
| 2 | A primary key attribute in a table can never contain a null value. | A foreign key attribute may have null values as well. | |||||||||||||||||||||||||||||||||||
| 3 | Not more than one primary key is permitted in a table. | A table can have one or more than one foreign key for referential purposes. | |||||||||||||||||||||||||||||||||||
| 4 | Duplicity is strictly prohibited in the primary key; there cannot be any duplicate values. | Duplicity is permitted in the foreign key attribute, hence duplicate values are permitted. | |||||||||||||||||||||||||||||||||||
| 5 | Example:
Consider the table student, which keeps record of students in a class: Here, Id is the primary key which uniquely identifies each record in the table “student”
|
Now, let us consider the table teacher, which records the teachers in the school:
Here Tid or teacher id is the unique primary key, for each record in the table. This table uses the “ID” attribute which is the primary key of the “student” table as its reference key or foreign key to refer to the student the particular teacher teaches, :
Since one student is taught by more than one teachers, the ID attribute (which is the foreign key in this table), contains duplicate values. |
The foreign key of one table although is derived from the primary key of the other table, holds completely different characteristics and these differences are crucial which should be taken care of to avoid any errors.
Comment below if you have queries related to primary key vs foreign key.
The post Difference between Primary Key and Foreign Key appeared first on The Crazy Programmer.
from The Crazy Programmer https://www.thecrazyprogrammer.com/2019/04/difference-between-primary-key-and-foreign-key.html
Comments
Post a Comment