Our mobile phone is one of the most important device, it has almost all of our crucial data stored in it. Losing the data can be really dreadful. Have you lost your Iphone data due to any accident or something like system crash, forgotten password or stolen or lost data? Well if you have then let me tell you that IMyFone D-back ensures you to get it back. Many a time’s users encounter virus attacks on their phones which makes them lose all their data. Earlier to get that data back was tough but not anymore with the IMyFone D-back. IMyFone D-Back offers four modes of recovery to gain your lost data.
Following are the Features
- It offers smart iphone data recovery to the users, and this is the best choice for the users who know even little about technology.
- It also assures the users to recover the data without any hassle or data theft from all the Iphone, ipad and iPod devices.
- Recovering back from the iTunes might seem impossible but not anymore, with iMyFone D-back one can recover their iTunes back-up to PC or Mac.
- With the iMyFone D-back one can even recover their data from the icloud backup without any restoring being required.
- This supports about 20 plus data types like whatsapp, Wechat and kik, messages and contacts etc.
- Not only this but it also fix’s various issues the IOS users encounter on a daily basis without any hassle or data loss.
The iMyFone D-back recovers the data in three simple steps which include connection of the device, scan and preview and select and recover the data.
Following is one of the methods which will help you to get your lost data back using the iMyFone D-back.
The very first step is to launch the iMyFone D- Back on your IOS device.
Now, from the smart recovery tab just click on the button start.
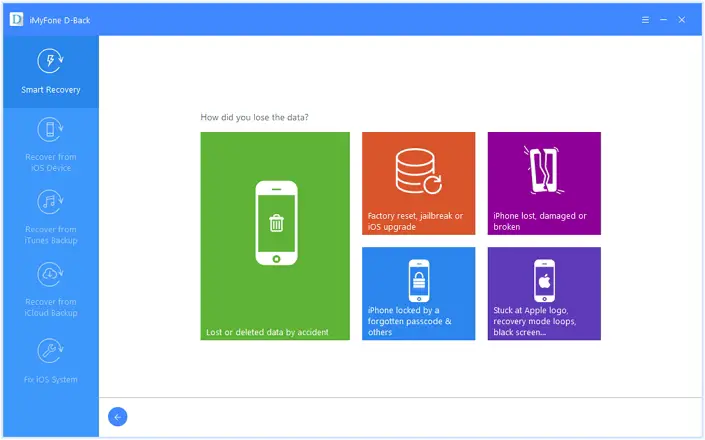
Choose the option which says about how you lost your data and that will make it easier for subsequent scan or memory.
The last step is just to scan and recover your lost iphones files and the iMyFone D-Back data recovery software will get all your data back.
Final Words
The reviews of the iMyFone D-back are positive; it has helped many people to get their precious data back on their device. With the amazing features it has to offer this is the best option you could try to get your data back.
The iMyFone D-back supports all the devices including iTunes and the latest IOS versions as well. The best part about this is that the user can even have a free trail before purchase to verify their performance.
They also offer a 100% security to their users as well they give a 30 day money back guarantee which is a win-win option for both.
With easy user interface and no complication in the process of recovery iMyFone D-back is definitely a good choice.
Thank you.
The post iMyFone D-Back iPhone Data Recovery appeared first on The Crazy Programmer.
from The Crazy Programmer https://www.thecrazyprogrammer.com/2017/12/imyfone-d-back-iphone-data-recovery.html
Comments
Post a Comment