 I've mentioned this tip before but once more for the folks in the back. This email productivity tip is a game-changer for most information workers.
I've mentioned this tip before but once more for the folks in the back. This email productivity tip is a game-changer for most information workers.
We all struggled with email.
- Some of us just declare Email Bankruptcy every few months. Ctrl-A, delete, right? They'll send it again.
- Some of us make detailed and amazing Rube Goldbergian email rules and deliberately file things away into folders we will never open again.
- Some of us just decide that if an email scrolls off the screen, well, it's gone.
Don't let the psychic weight of 50,000 unread emails give you headaches. Go ahead, declare email bankruptcy - you're already in debt - then try this one email rule.
One Email Rule
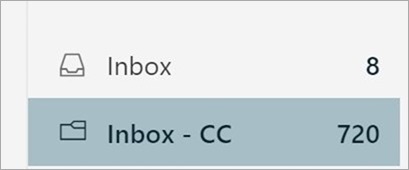
Email in your inbox is only for email where you are on the TO: line.
All other emails (BCC'ed or CC'ed) should go into a folder called "Inbox - CC."
That's it.
I just got back from a week away. Look at my email there. 728 emails. Ugh. But just 8 were sent directly to me. Perhaps that's not a realistic scenario for you, sure. Maybe it'd be more like 300 and 400. Or 100 and 600.
Point is, emails you are CC'ed on are FYI (for your information) emails. They aren't Take Action Now emails. Now if they ARE, then you need to take a moment and train your team. Very simple, just reply and say, "oops, I didn't see this immediately because I was cc'ed. If you need me to see something now, please to: me." It'll just take a moment to "train" your coworkers because this is a fundamentally intuitive way to work. They'll say, "oh, make sense. Cool."
Try this out and I guarantee it'll change your workflow. Next, do this. Check your Inbox - CC less often than your Inbox. I check CC'ed email a few times a week, while I may check Inbox a few times a day.
If you like this tip, check out my complete list of Productivity Tips!
Sponsor: Unleash a faster Python Supercharge your applications performance on future forward Intel® platforms with The Intel® Distribution for Python. Available for Windows, Linux, and macOS. Get the Intel® Distribution for Python* Now!
© 2017 Scott Hanselman. All rights reserved.
from Scott Hanselman's Blog http://feeds.hanselman.com/~/527651914/0/scotthanselman~One-Email-Rule-Have-a-separate-Inbox-and-an-Inbox-CC-to-reduce-email-stress-Guaranteed.aspx
Comments
Post a Comment