You realize that you need a VPN. The decision that you have to make is if you want to set up a VPN or if you want to use a VPN provider. If you go the provider route, the provider may ask you to choose the protocol you want. Or if you set up a VPN, you need to know which protocol you will use. In this article we are going to take a look at some of the more popular protocol standards to help you get an idea of which one you should consider using.

PPTP
This is a popular standard for VPN connections. It’s going to be difficult for you to find a VPN provider that does not offer PPTP connections. PPTP is Point-To-Point Tunneling Protocol. This VPN protocol first came on the scene back in 1995, although its development dates back more than a decade before it’s public release.
PPTP was designed based on the previous PPP standard. The PPP standard did not have a safe tunneling feature. When it was first introduced, PPTP was a Windows system protocol. However, it quickly became popular as a VPN protocol being used on a variety of platforms.
As a VPN protocol, PPTP laid out the guidelines that guaranteed that VPN client to VPN server communications were secure and were handled correctly.
With PPTP, the client creates a connection known as the tunnel. All of your online data and online traffic travels through this tunnel where it is secured and encrypted simultaneously. It is able to create a secure server connection with only the server address, password, and username. PPTP works across a number of platforms. It can be used on multiple operating systems and devices. PPTP will use General Routing Encapsulation, IP port 47 and TCP port 1723.
PPTP supports voluntary tunneling as well as compulsory tunneling. Voluntary tunneling is where the tunneling is initiated by the client. This means that ISP bridge support is not needed. Compulsory tunneling is where the tunneling is initiated by the PPTP server. Therefore, network access server support and broader access service support is required.

PPTP was considered to be exceptionally secure. That is not the case today. There is documentation to support the fact that agencies working with the US government, including the NSA, have been able to crack PPTP traffic. This, along with other known security vulnerabilities, makes PPTP a prime target for hackers.
PPTP makes it possible to have a fast connection. This allows you to use a VPN without significantly lowering your online speeds. For a simplified explanation of how VPNs work check this.
OpenVPN
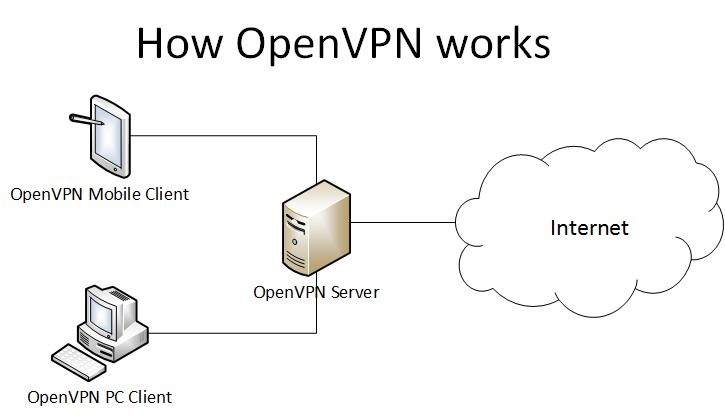
OpenVPN creation stems back to the year 2002. It was initially founded by James Yonan. This protocol has become exceptionally popular because it supports the major operating systems, including Linux, Windows, and Mac OS. It also works well with mobile platforms, including Android and iOS.
The reason why a person wants a VPN security protocol is because they want a high level of security. OpenVPN excels at this. One of the reasons is its 256 bit encryption thanks to OpenSSL. OpenVPN is not only secure, but it is also flexible and works well with third-party software. There are a number of OpenVPN providers that use this protocol to make commercially available VPNs for clients and users.
OpenVPN can take advantage of two different protocols, which are UDP and TCP. TCP, also known as Transmission Control Protocol, is popular and commonly used thanks to its dependability, reliability, and ability to correct errors.
OpenVPN is a protocol that is commonly used to bypass encryption firewalls. One of the great examples of this is the Great Firewall in China. The OpenVPN protocol has been able to circumnavigate DPI, also known as Deep Packet Inspection, which is commonly used in China. DPI is a monitoring technology that is designed to inspect passing traffic in real-time. However, OpenVPN can cloak traffic.
One of the biggest benefits of OpenVPN is the fact that it is open source. Other VPN protocols are owned by mega companies. The OpenVPN protocol is open, freely available for modification, and is backed by a large community that is active in filing bug reports, allowing developers to improve the source code as well as to create regular updates.
L2TP
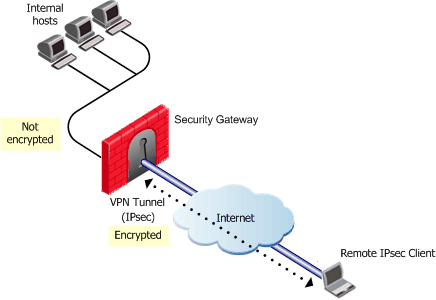
L2TP also known as Layer 2 Tunnel Protocol. It is a VPN protocol that does not have encryption. That’s why you will commonly see it referred to as L2TP/IPsec, with the IPsec providing the encryption. L2TP protocol is built into most desktop operating systems as well as the operating systems of mobile devices. This makes it relatively easy to implement.
A downside is that since it uses UDP port 500, L2TP cannot be disguised on other ports like you can with OpenVPN. As a result, L2TP is a lot easier to block and is not as effective at getting around firewalls as other forms of VPN protocols.
In theory, IPsec should be secure. However, it is rumored that the NSA has weakened this encryption standard. Of course, there’s no way to know for sure. However, you couple this with the fact that L2TP is a slower protocol because the traffic must first be converted into L2TP and then encrypted with IPsec and it is clear to see why this is not the fastest VPN protocol on the market.
Which Option Is Best?
The answer is going to vary depending on why you want to use the VPN. However:
- OpenVPN is generally considered to be your best bet. This is the same protocol used for most free VPNs. It is fast, secure, and flexible. It is going to work for you regardless of the operating system you use or the platform you use.
- PPTP is going to be easy for you to set up, and it is going to give you a fast connection. That being said, it is insecure.
- L2TP/IPSec is an improvement from PPTP. But since it is a two-step process, it is slower and the security of it is questionable.
Which protocol do you use for your VPN? We would love to hear from you. Let us know your thoughts the comment section below.
The post OpenVPN vs PPTP vs L2TP – VPN Protocols Comparison appeared first on The Crazy Programmer.
from The Crazy Programmer https://www.thecrazyprogrammer.com/2019/03/openvpn-vs-pptp-vs-l2tp.html
Comments
Post a Comment