An operating system is the basic mechanism behind the working of the computer systems and mobile devices and so, understanding the operating system becomes very important from a user’s perspective. The various types of Operating systems are as follows:
Types of Operating System
1. Batch Operating System
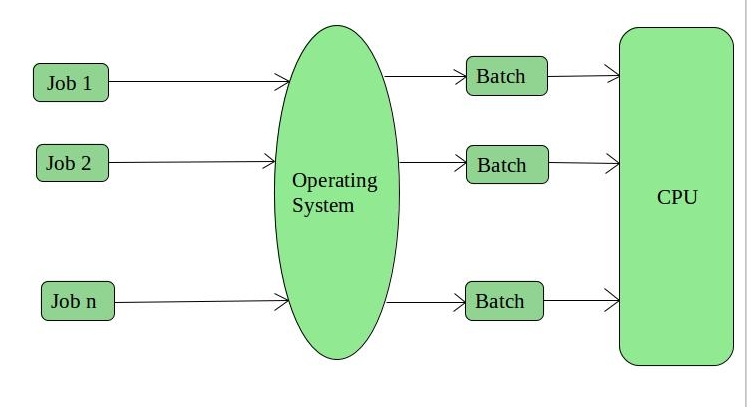
As, is very clear from the name itself, a batch operating system works by grouping the jobs into batches, hence the CPU does not directly interacts with the jobs, instead it interacts with the batches which are created by the operating system on the basis of similarities among them.
It supports multiple users and the idle time of the CPU is very less. Since, it works by grouping multiple jobs into lesser number of batches, managing a large amount of work becomes easy in a batch operating system. However, batch operating systems are costly and debugging is harder.
Example: Payroll systems, Bank statements etc.
2. Time-Sharing Operating System
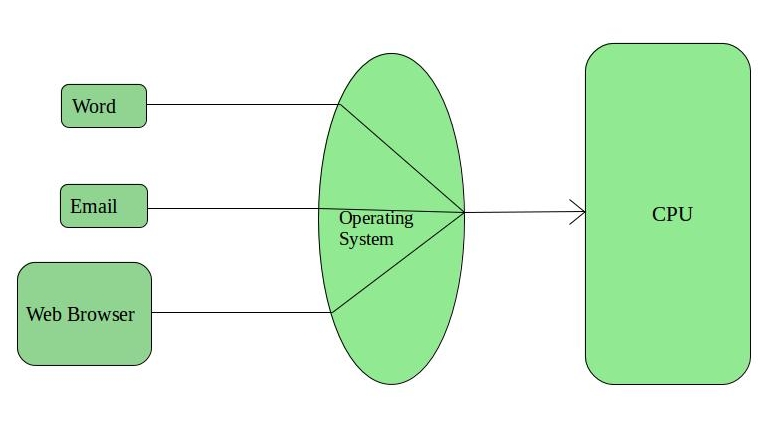
In the time sharing operating systems, a certain time limit “quantum” is assigned to each one of the jobs. After the completion of one job, the other one is assigned the time. Hence, each job gets equal time in the CPU.
Often, these systems have a data communication problem, however.
Examples: Unix, Multics etc.
3. Network Operating System
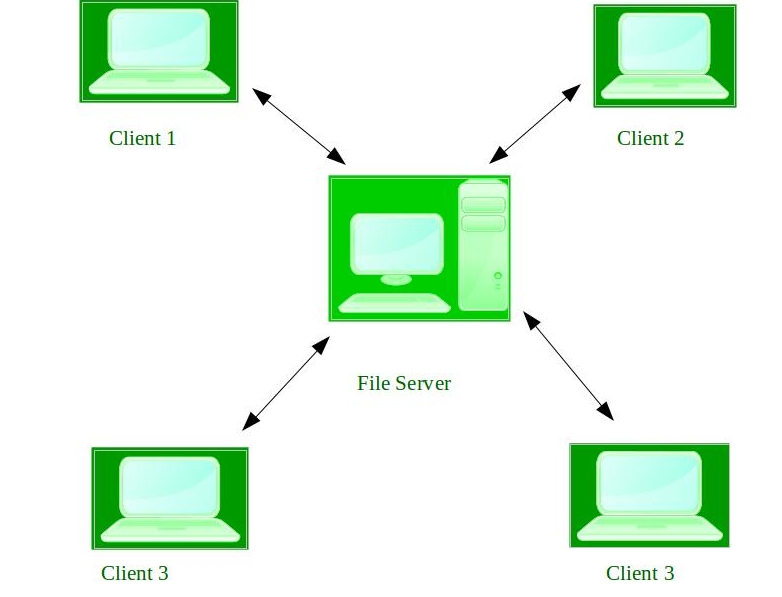
They too work on an interconnection model but this model comprises of a client-server like small private network.
Unlike the distributed systems which are loosely coupled, the network operating systems are tightly coupled systems. This means that all the computers connected to the centralized server know the configurations, connections etc. These connections and the network are quite stable and the different systems located at various locations can easily access the server and hence the sharing of files can be done easily. But the cost of the server and maintenance and other updates are considerably high.
Example: UNIX, Linux, Novell Netware, Microsoft Windows server 2003 etc.
4. Distributed Operating System
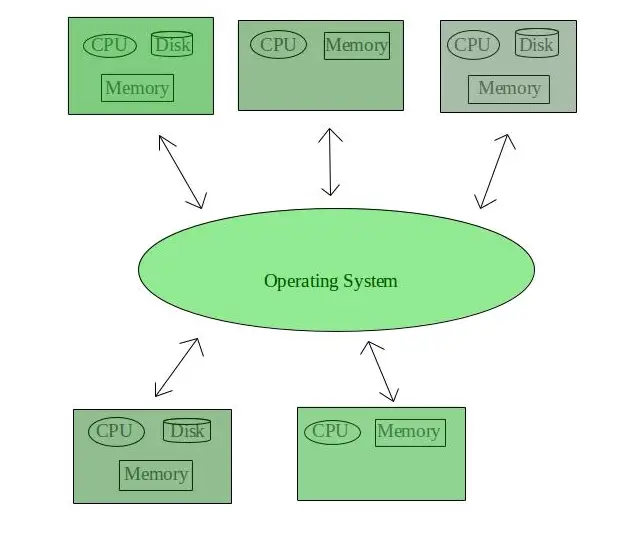
The distributed operating systems, allow the interconnection of various systems all over the world using a shared communication network. We can share documents anywhere on the network.
However, all the interconnected systems are independent and hence, the failure of one won’t affect any other system in the network. The computation tasks are also fast and the load on just one computer is reduced.
Example: LOCUS.
5. Real Time Operating System
The real time operating systems are known for their quick processing of inputs and correspondence. These systems have to work quickly because even a small delay in the response results in failure. So, they work as if working in real time and absolutely no time is required for processing.
The real time operating systems are further divided into two categories:
- Hard Real Time Operating System
In these systems, even a small delay in time period can lead to major destructions. Hence, the response time (the time required to respond to inputs) must not exceed more than the time which is safe.
These are used in missile launching systems, automatic parachutes, etc.
- Soft Real Time Operating System
In these systems, the time constraint is not that severe and delays in response might not lead to destruction, however, the system still is considered to be failing. These are used in software application developments like games and other software where immediate user interaction is involved.
These real time operating systems are error free and memory is allocated excellently in them, also the current running application is in focus while the others in queue are not much considered. But, they use very complex algorithms and heavy system resources.
Source: https://www.geeksforgeeks.org/operating-system-types-operating-systems-awaiting-author/
The operating system is a program on which the other software runs, and a clear understanding of them can be made through the above points.
The post Types of Operating System appeared first on The Crazy Programmer.
from The Crazy Programmer https://www.thecrazyprogrammer.com/2019/03/types-of-operating-system.html
Comments
Post a Comment